3. Security
A secutiry of the system is a very important aspect of the system. All security systems are based on authentication and authorization.
-
Authentication is the process of verifying the identity of a user.
-
Authorization is the process of verifying what the user has access to.
flowchart LR
subgraph api [Trusted Layer]
direction TB
gateway --> account
gateway --> others
gateway e4@==> auth:::red
auth e2@==> account
account --> db@{ shape: cyl, label: "Database" }
others --> db
end
internet e1@==>|request| gateway:::orange
e1@{ animate: true }
e2@{ animate: true }
e4@{ animate: true }
classDef red fill:#fcc
classDef orange fill:#FCBE3EclassDiagram
namespace auth {
class AuthController {
+register(RegisterIn RegisterIn): TokenOut
+login(LoginIn loginIn): TokenOut
}
class RegisterIn {
-String name
-String email
-String password
}
class LoginIn {
-String name
-String email
}
class TokenOut {
-String token
}
class SolveOut {
-String idAccount
}
}
namespace auth-service {
class AuthResource {
+register(RegisterIn RegisterIn) TokenOut
+login(LoginIn loginIn) TokenOut
}
class AuthService {
+register(Register) Regiter
+login(LoginIn loginIn) String
}
class Register {
-String id
-String name
-String email
-String password
}
}
<<Interface>> AuthController
AuthController ..> RegisterIn
AuthController ..> LoginIn
AuthController ..> TokenOut
AuthController <|-- AuthResource
AuthResource *-- AuthService
AuthService ..> RegisterAuth
📁 api
└── 📁 auth
├── 📁 src
│ └── 📁 main
│ └── 📁 java
│ └── 📁 store
│ └── 📁 auth
│ ├── 📄 AuthController.java
│ ├── 📄 LoginIn.java
│ ├── 📄 RegisterIn.java
│ ├── 📄 SolveOut.java
│ └── 📄 TokenOut.java
└── 📄 pom.xml
Source
Auth-Service
📁 api
└── 📁 auth-service
├── 📁 src
│ ├── 📁 main
│ │ └── 📁 java
│ │ └── 📁 store
│ │ └── 📁 auth
│ │ ├── 📄 AuthApplication.java
│ │ ├── 📄 AuthParser.java
│ │ ├── 📄 AuthResource.java
│ │ ├── 📄 AuthService.java
│ │ ├── 📄 JwtService.java
│ │ └── 📄 Register.java
│ └── 📁 resources
│ └── 📄 application.yaml
├── 📄 pom.xml
└── 📄 Dockerfile
Source
Body
Sequence Diagram
sequenceDiagram
autonumber
actor User
User->>+Auth: register (RegisterIn)
Auth->>+Account: create (AccountIn)
Account->>-Auth: returns the new account (AccountOut)
Auth->>-User: returns 201 (TokenOut)Body
Sequence Diagram
sequenceDiagram
autonumber
actor User
User->>+Auth: authenticate (LoginIn)
Auth->>+Account: findByEmailAndPassword
critical validated
Account->>-Auth: returns the account
option denied
Auth-->>User: unauthorized message
end
Auth->>Auth: generates a token
Auth->>-User: returns TokenOut
User->>User: stores the token to use for the next requestsSecurity
Security is an important aspect of software development. It involves protecting the confidentiality, integrity, and availability of data and resources. Two key concepts in security are authentication and authorization.
Authentication
Authentication is the process of verifying the identity of a user or system. It ensures that the user or system is who they claim to be. Common authentication methods include passwords, biometrics, and two-factor authentication. The system checks these credentials against the stored data. If the credentials are valid, the system confirms the user's identity.
In many systems, after successful authentication, the system generates a token. This token is a piece of data that represents the user's authentication session. It's like a digital ticket that proves the user's identity for a certain period of time.
This token is then sent back to the user. The user's client software (like a web browser) stores this token and sends it along with every subsequent request to the server (in case of stateless server). This way, the server knows that the request comes from an authenticated user without needing to ask for the credentials again.
Here's a simplified step-by-step process:
sequenceDiagram
autonumber
actor User
User->>+Auth Service: authentication(credentials)
Auth Service->>Auth Service: verifies credenditals and generates a token
Auth Service->>-User: returns the token
User->>User: stores the token to use for the next requests- The user sends their username and password (or other credentials) to the server;
- The server verifies the credentials. If they're valid, the server generates a token.
- The server sends this token back to the user.
- The user's client software stores this token.
- For every subsequent request, the client sends this token along with the request.
- The server checks the token to ensure it's valid and hasn't expired.
- This token-based authentication process is commonly used in many modern web applications and APIs. It helps maintain the user's session and allows the server to authenticate requests without storing the user's state.
Authorization
Authorization is the process of granting or denying access to specific resources or actions based on the authenticated user's privileges. It determines what a user is allowed to do within a system. Authorization can be role-based, where permissions are assigned based on predefined roles, or attribute-based, where permissions are based on specific attributes of the user.
In many systems, the token not only represents the user's identity, but also includes information about their permissions or roles. This is often done using a type of token called a JSON Web Token (JWT), which can include a payload of data.
Here's a simplified step-by-step process:
sequenceDiagram
autonumber
actor User
User->>Auth Service: request with token
Auth Service->>Auth Service: decodes the token and extracts claims
Auth Service->>Auth Service: verifies permissions
critical allowed
Auth Service->>Secured Resource: authorizes the request
Secured Resource->>User: returns the response
option denied
Auth Service-->>User: unauthorized message
end - After authentication, the user's client software sends a request to a server. This request includes the token.
- The server decodes the token and extracts the user's identity and permissions.
- The server checks whether the user has the necessary permissions for the requested action. This could involve checking the user's roles or other attributes against the requirements for the action.
- If the user has the necessary permissions, the server allows the action. If not, the server denies the action.
This process allows the server to authorize actions without needing to repeatedly look up the user's permissions. It also allows for stateless servers, as the necessary information is included in every request.
By implementing strong authentication and authorization mechanisms, software systems can ensure that only authorized users have access to sensitive data and functionalities, reducing the risk of unauthorized access and potential security breaches.
As the platform has only one entrace point, it is
JWT is a decentralized
The point of entrance of API is the gateway, then as suggested by 8.
The gateway is responsible for the security of the system. It is the first point of contact for all incoming requests. The gateway is responsible for routing requests to the appropriate services and ensuring that only authorized users can access the system.
sequenceDiagram
autonumber
actor User
User->>Gateway: route(ServerHttpRequest)
Gateway->>+AuthorizationFilter: filter(ServerWebExchange, GatewayFilterChain)
AuthorizationFilter->>RouteValidator: isSecured.test(ServerHttpRequest)
RouteValidator-->>AuthorizationFilter: True | False
critical notSecured
AuthorizationFilter->>Gateway: follow the flux
end
AuthorizationFilter->>AuthorizationFilter: isAuthMissing(ServerHttpRequest)
critical isAuthMissing
AuthorizationFilter->>User: unauthorized message
end
AuthorizationFilter->>AuthorizationFilter: validateAuthorizationHeader()
critical isInvalidAuthorizationHeader
AuthorizationFilter->>User: unauthorized message
end
AuthorizationFilter->>Auth: solve(Token)
critical isInvalidToken
Auth->>User: unauthorized message
end
Auth->>AuthorizationFilter: returns SolveOut
AuthorizationFilter->>AuthorizationFilter: updateRequestHeader(ServerHttpRequest)
AuthorizationFilter->>Gateway: follow the fluxGateway-Service
📁 api
└── 📁 gateway-service
├── 📁 src
│ └── 📁 main
│ ├── 📁 java
│ │ └── 📁 store
│ │ └── 📁 gateway
│ │ ├── 📄 GatewayApplication.java
│ │ ├── 📄 GatewayResource.java
│ │ └── 📁 security
│ │ ├── 📄 AuthorizationFilter.java
│ │ ├── 📄 CorsFilter.java
│ │ ├── 📄 RouterValidator.java
│ │ ├── 📄 SolveOut.java
│ │ └── 📄 TokenOut.java
│ └── 📁 resources
│ └── 📄 application.yaml
├── 📄 pom.xml
└── 📄 Dockerfile
Source
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 | |
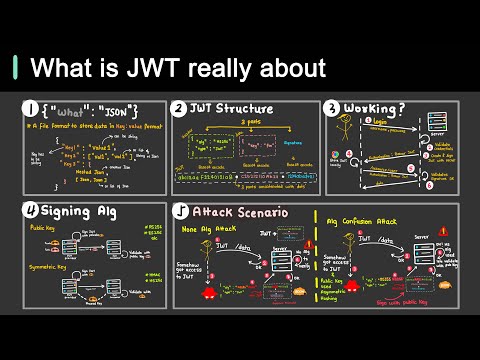
JWT - JSON Web Token
JWT stands for JSON Web Token. It is a compact, URL-safe means of representing claims between two parties. JWTs are commonly used to secure the transmission of information between parties in a web environment, typically for authentication and information exchange. The JWT specification is defined by RFC 75191 and it is a decentralized approach for security (which can support horizontal scalability).
Here are the key components and concepts of JWT:
- JSON Format: JWTs are represented as JSON objects that are easy to parse and generate. The JSON format makes them human-readable and easy to work with.
-
Three Parts: JWTs consist of three parts separated by dots (
.): Header, Payload, and Signature.-
Header: The header typically consists of two parts: the type of the token (JWT) and the signing algorithm being used, such as HMAC SHA256 or RSA.
-
Payload: The payload contains the claims. Claims are statements about an entity (typically, the user) and additional data. There are three types of claims: registered, public, and private claims.
-
Signature: To create the signature part, you take the encoded header, the encoded payload, a secret, the algorithm specified in the header, and sign that.
-
-
Encoding: Each of the three parts is Base64Url encoded, and the resulting strings are concatenated with periods between them. The final JWT looks like:
xxxxx.yyyyy.zzzzz. - Stateless and Self-contained: JWTs are stateless, meaning that all the information needed is within the token itself. The server doesn't need to store the user's state. They are also self-contained, meaning that all the information needed is contained within the token.
- Use Cases: JWTs are commonly used for authentication and information exchange between parties. For example, after a user logs in, a server could generate a JWT and send it to the client. The client can then include the JWT in the headers of subsequent requests to access protected resources. The server can verify the authenticity of the JWT using the stored secret key.
- Security Considerations: While JWTs are widely used and versatile, it's important to handle them securely. For instance, the key used to sign the JWT should be kept secret, and HTTPS should be used to transmit JWTs to prevent man-in-the-middle attacks.
Here's a simple example of a JWT created on JWT Builder2:
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzUxMiJ9.eyJpc3MiOiJJbnNwZXIiLCJpYXQiOjE3MDMwMDgzMzgsImV4cCI6MjAxODU0MTEzOCwiYXVkIjoid3d3Lmluc3Blci5lZHUuYnIiLCJzdWIiOiJodW1iZXJ0b3JzQGluc3Blci5lZHUuYnIiLCJHaXZlbk5hbWUiOiJIdW1iZXJ0byIsIlN1cm5hbWUiOiJTYW5kbWFubiIsIkVtYWlsIjoiaHVtYmVydG9yc0BpbnNwZXIuZWR1LmJyIiwiUm9sZSI6IlByb2Zlc3NvciJ9.SsGdvR5GbYWTRbxY7IGxHt1vSxhkpRueBJWsi0lrPhJVCICp119QjU8F3QvHW0yF5tw-HhQ9RVh0l89t4M0LNw
This JWT consists of three parts, decoded by 3:
eyJpc3MiOiJJbnNwZXIiLCJpYXQiOjE3MDMwMDgzMzgsImV4cCI6MjAxODU0MTEzOCwiYXVkIjoid3d3Lmluc3Blci5lZHUuYnIiLCJzdWIiOiJodW1iZXJ0b3JzQGluc3Blci5lZHUuYnIiLCJHaXZlbk5hbWUiOiJIdW1iZXJ0byIsIlN1cm5hbWUiOiJTYW5kbWFubiIsIkVtYWlsIjoiaHVtYmVydG9yc0BpbnNwZXIuZWR1LmJyIiwiUm9sZSI6IlByb2Zlc3NvciJ9
JWTs are widely used in web development due to their simplicity, flexibility, and support across various programming languages and frameworks. They are commonly used in token-based authentication systems.
Addtional Material
-
Autenticação e Autorização com Spring Security e JWT Tokens by Fernanda Kipper
-
RFC 7519 - JSON Web Token (JWT), 2015. ↩
-
DELANTHA, R., Spring Cloud Gateway security with JWT, 2023. ↩
-
PGzlan, Serve your hash with Salt and Pepper for Stronger Account Security, 2023. ↩
-
DELANTHA, R., Spring Cloud Gateway security with JWT, 2023. ↩